We keep your
crown jewels safe.
Always.
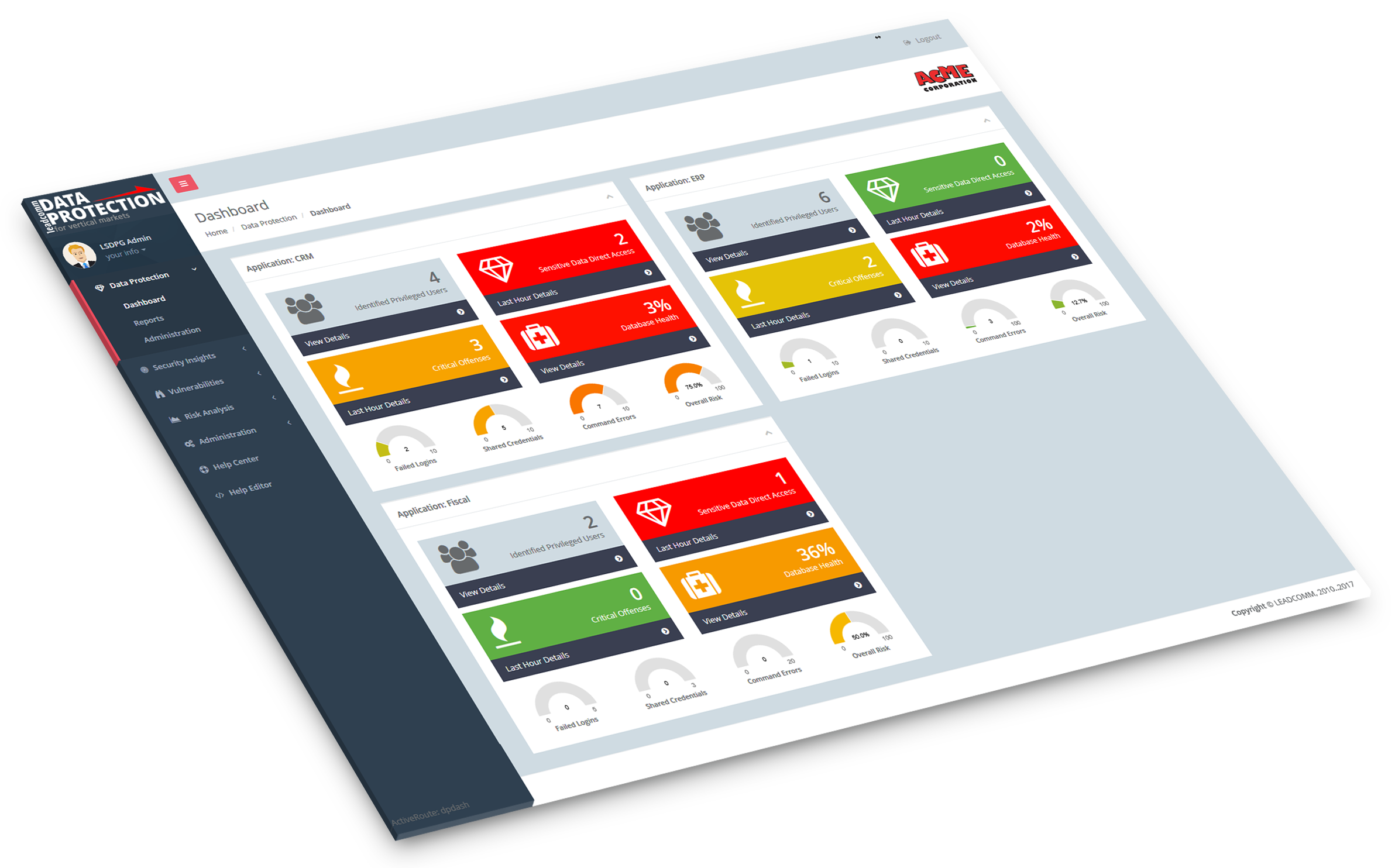
Meet the LEADCOMM DATA PROTECTION for Vertical Markets solution.
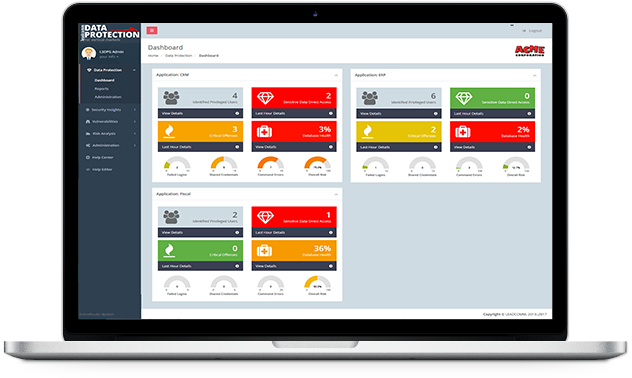
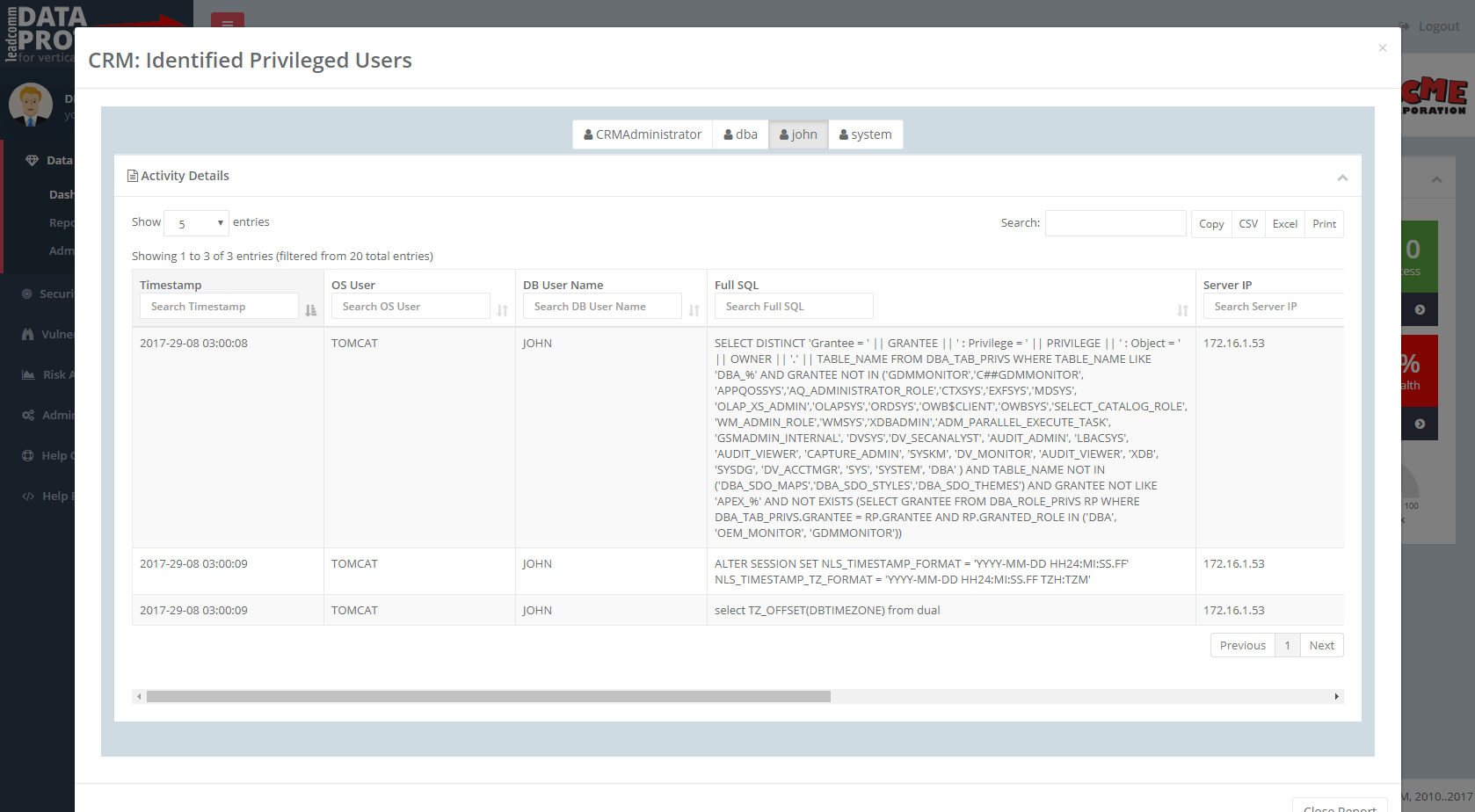
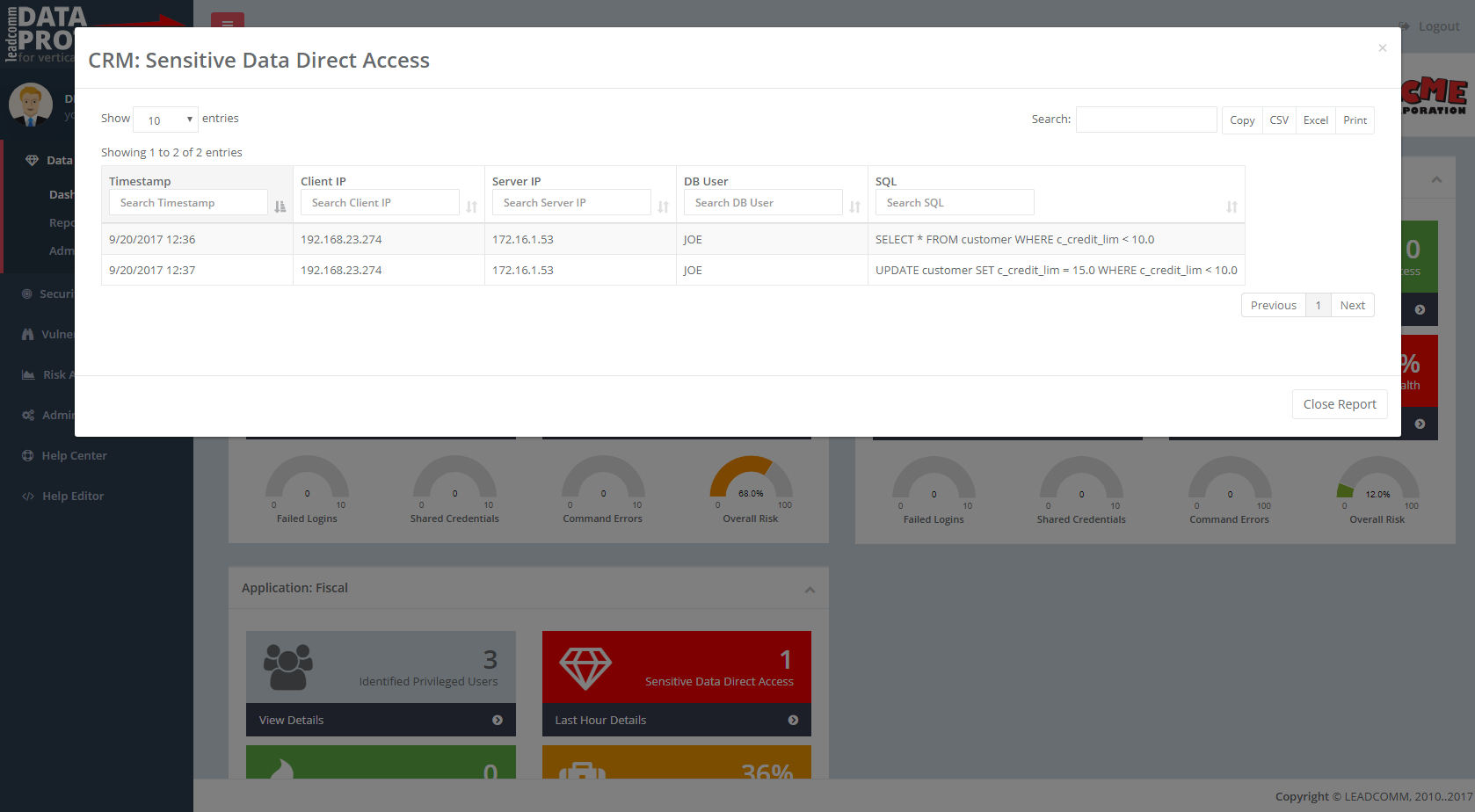
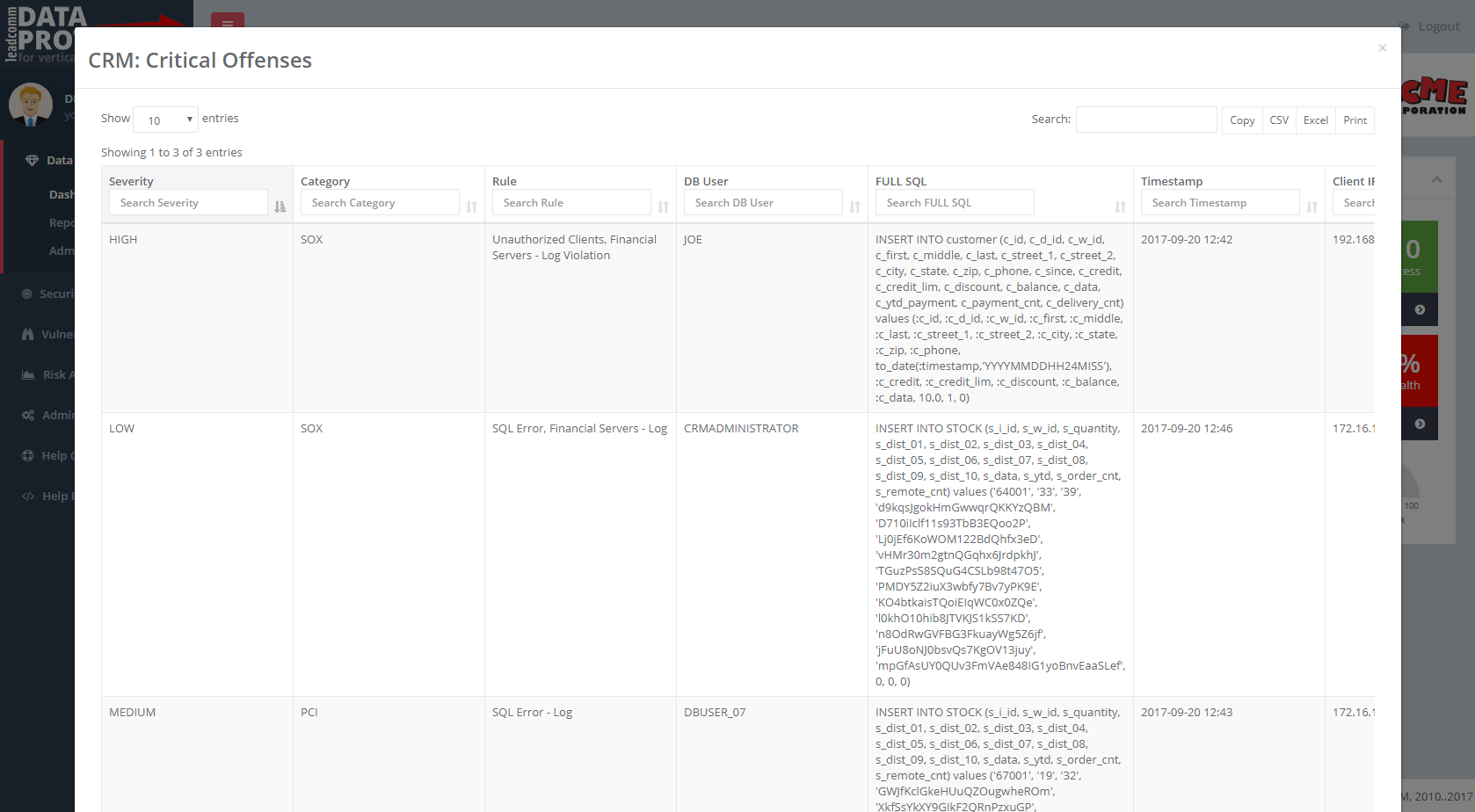
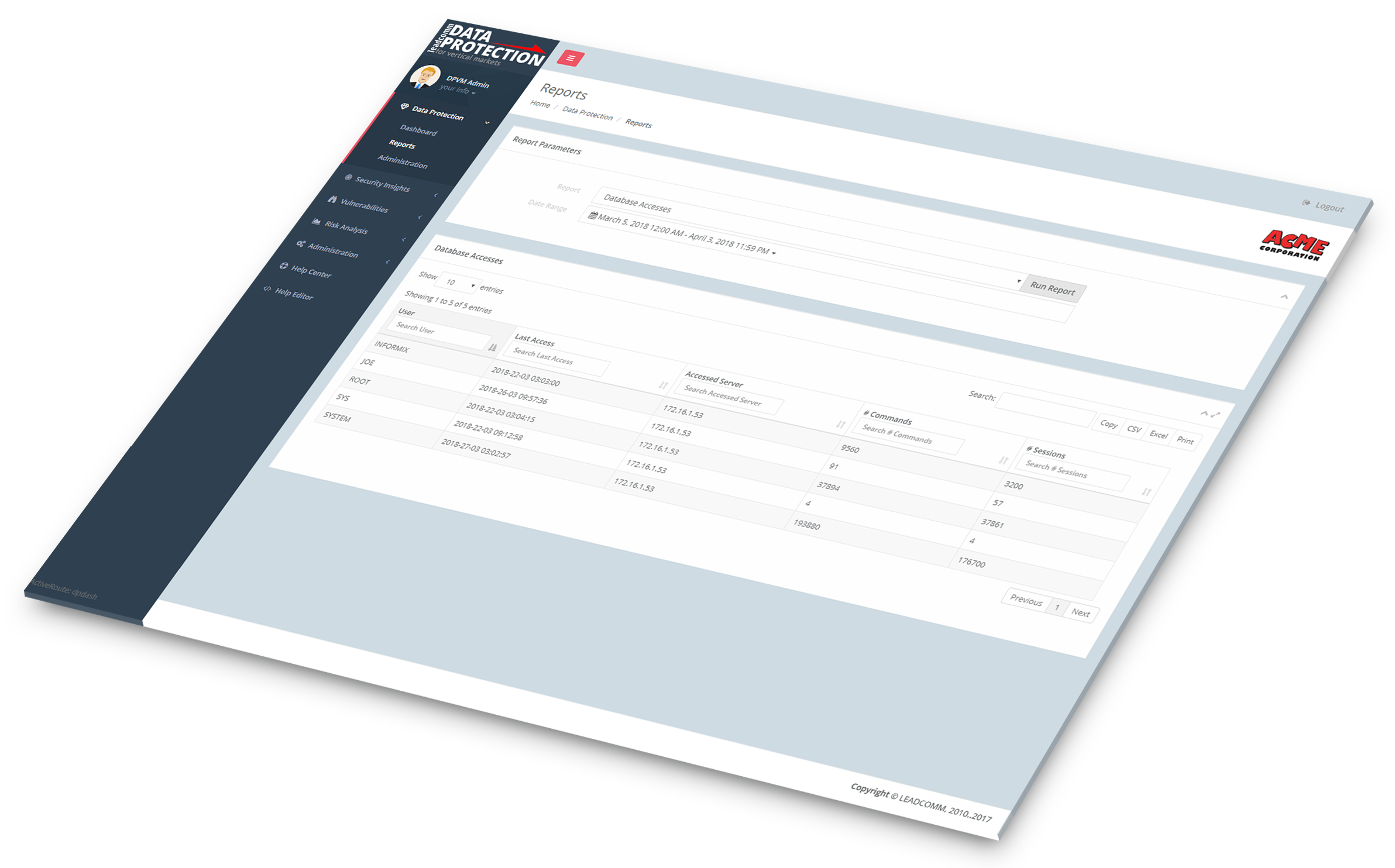
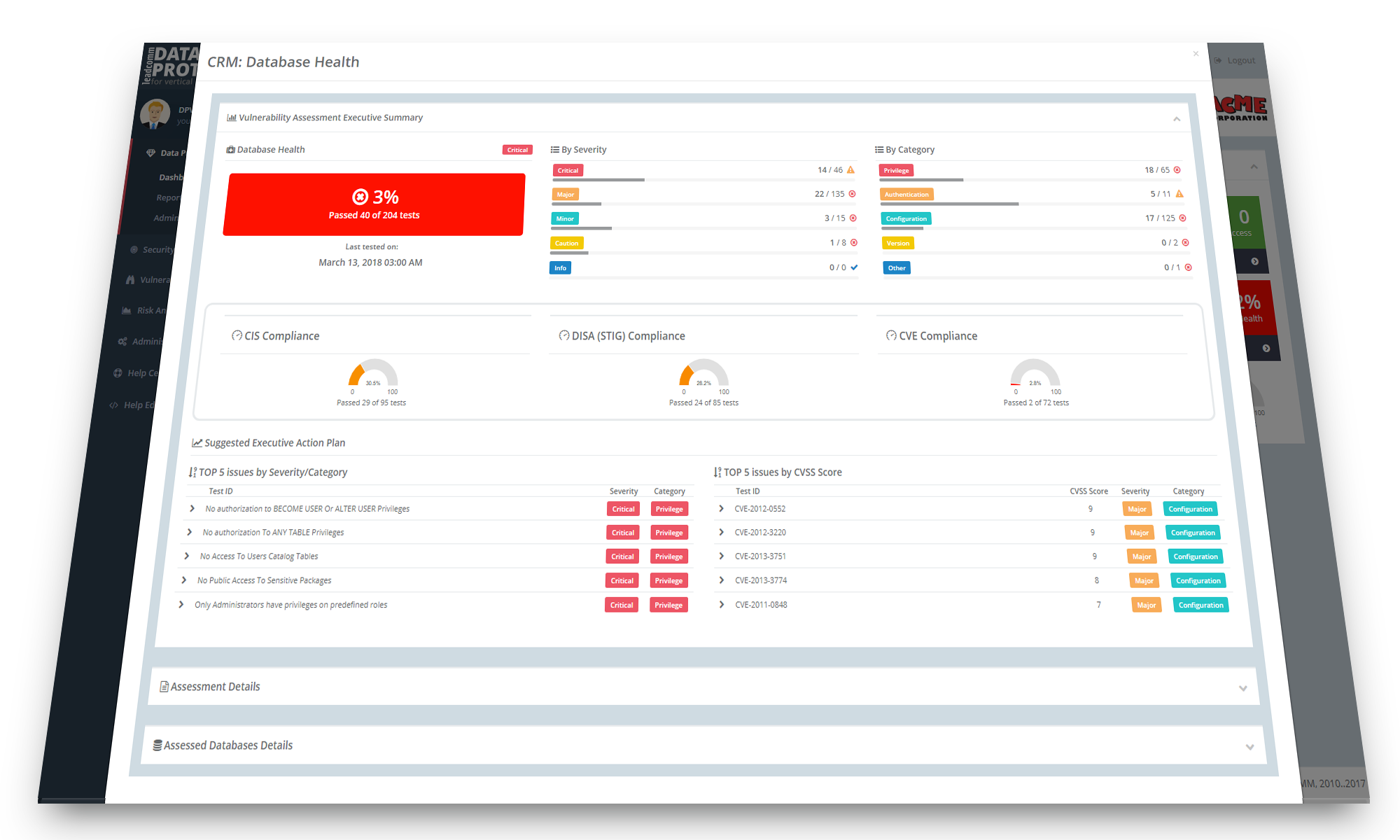
Be aware of your
data security
wherever you are.
Our modern interface works on any kind of device.